Secure Remote Access
Provides secure, context-aware internet access while protecting against unauthorized access and data breaches.
navbar works!
Secure users, devices, and applications with identity-based
access without exposing your network.

An alternative to VPN that securely authenticates the user and seamlessly connects the device to the Cloud through reliable, high performance and encrypted tunnels that offers security, faster access, enhanced user experience, and easy setup

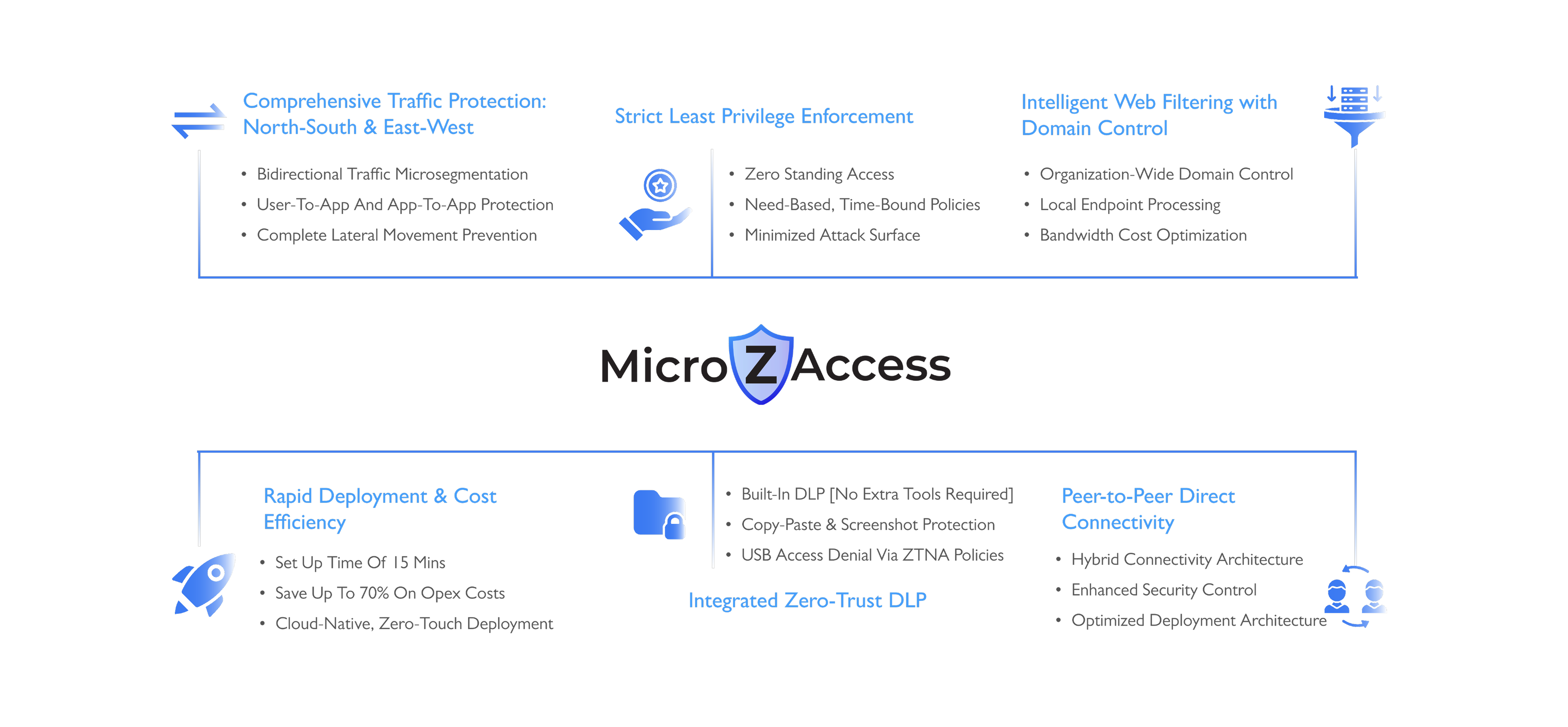
80% Reduction in Attack Surface

Set-up time 15 minutes

70% Lower OpEx Cost

4x Invisible - not vulnerable to DDoS attacks.

Authentication and Authorization
MFA-based user verification, device trust checks, and group policy matching before access is ever granted
Establish Encrypted Tunnel
MicroZAccess creates a dynamic, app-specific encrypted tunnel between the user and the target resource nothing else is exposed publicly.
Apply Risk-Based Policies
Policies adapt in real-time based on identity, device, time, location, and behavioral risk.
Enforce Access & Monitor
Apps stay invisible by default. MicroZAccess inspects traffic, filters risks, and continuously monitors for threats preventing lateral movement.


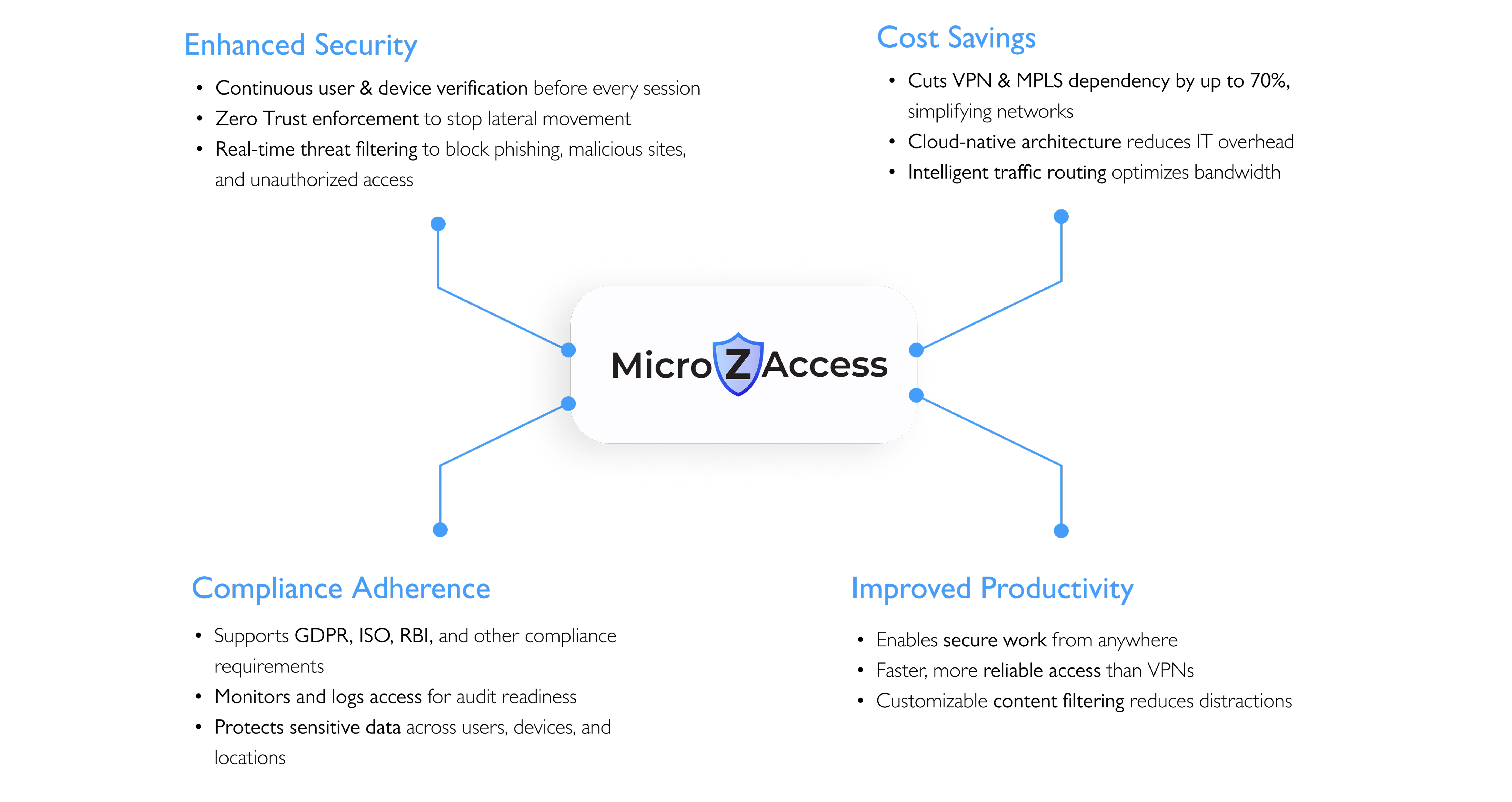
Adaptive, risk-based verification for every user
Real-time MFA & device posture checks
Advanced filtering blocks threats
Ensures secure and compliant browsing
Comprehensive access monitoring
Seamless API integration with security tools
Automated policy management
Integrated threat response workflows
Ongoing user and device validation
Strict least-privilege access enforcement
Isolates critical applications from threats
Prevents lateral movement within the network
Provides secure, context-aware internet access while protecting against unauthorized access and data breaches.
Secures sensitive data with granular external access controls and audit logs for visibility and investigation.
Secures DevOps and multi-cloud infrastructure through verified identities and enforced access controls.
Uses micro-segmentation to enforce granular access policies and meet industry compliance requirements.

Controls third-party access using identity- and role-based policies to reduce risk exposure.